Darkside is ransomware notorious for attacking high-profile industrial control systems and facilities. Its most famous attack was against the Colonial Pipeline line in the United States between May 6 – and May 12, 2021. This attack showcased how dangerous ransomware can be and the effect these attacks can have on the country and the world. This blog post is an analysis of Darkside.
Analysis
Darkside utilizes a lot of dynamic allocation as means to hide its functionality. This is done with the usage of LoadLibrary and GetProcessAddress functions. What makes this so tricky is their usage of encrypted strings, which have to go through a decryption process first. This added to the complexity and could be statically resolved. Dynamic analysis was necessary.
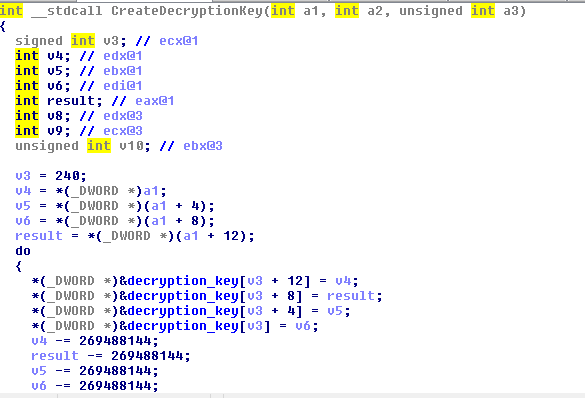
The decryption process is done entirely by using the key created through this function. Taking in two more minor 16-length keys, it makes a 256-byte decryption key, which is utilized through the entire malware to allocate and resolve strings and APIs dynamically. Because of the constant value of the key, the key is a great host base indicator as long as new versions do not change these.


The APIs are resolved here, looping through dword values and setting them accordingly. Afterward, the dword values are as follows:

What made Darkside ransomware so interesting was its usage of a UAC bypass to encrypt. UAC stands for User Access Control and bypassing it gives a program more control and privileges. Darkside utilized a COM object to achieve these higher privileges in this case. Note the following.

Darkside is initially executed but almost immediately executes the COM object CMSTPLUA. This being generated in a very specific way; C:\Windows\system32\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7}. Was is important about this COM object is that it is given higher privileges because it is listed under trusted COM by Windows. It then executes a ShellExecute function on Darkside, running it now in higher privileges.
A list of Approved COM is listed in the registry: Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\UAC\COMAutoApprovalList.
This is all my analysis as taken from this piece of malware. This malware is interesting because of its ability to escalate its privilege with relative ease and less noise than other means. Like most security exploits, utilizing the trust placed in other resources was the downfall here, as Darkside could capitalize on this and proceed with the encryption process and steal money accordingly.
💬 Comment: